The Enhanced Firewall feature in AVG Antivirus monitors the network traffic between your PC and the outside world to help protect you from unauthorized communication and intrusions. This feature is designed to require minimal input from you. To ensure you have protection, all you need to do is keep Enhanced Firewall enabled.
Manage apps
Enhanced Firewall controls when the apps on your PC can connect to the internet or to other networks. Enhanced Firewall creates default rules for an app when it starts for the first time.
To manually specify how Enhanced Firewall handles connection attempts from individual apps:
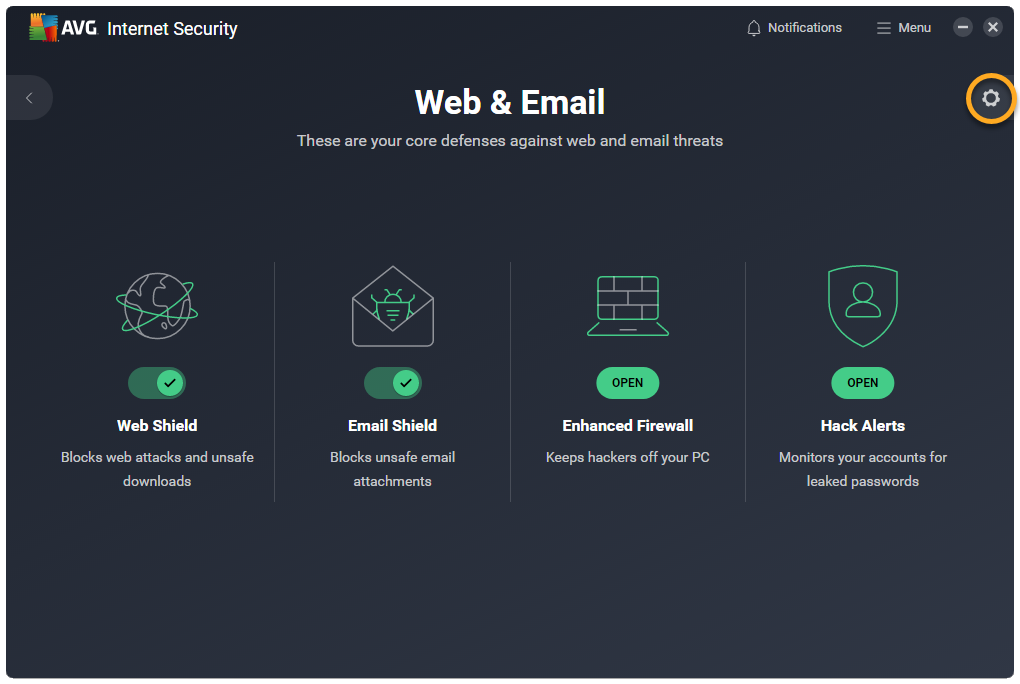
- Open AVG Antivirus and select the Web & Email tile.

- Click Open above Enhanced Firewall.

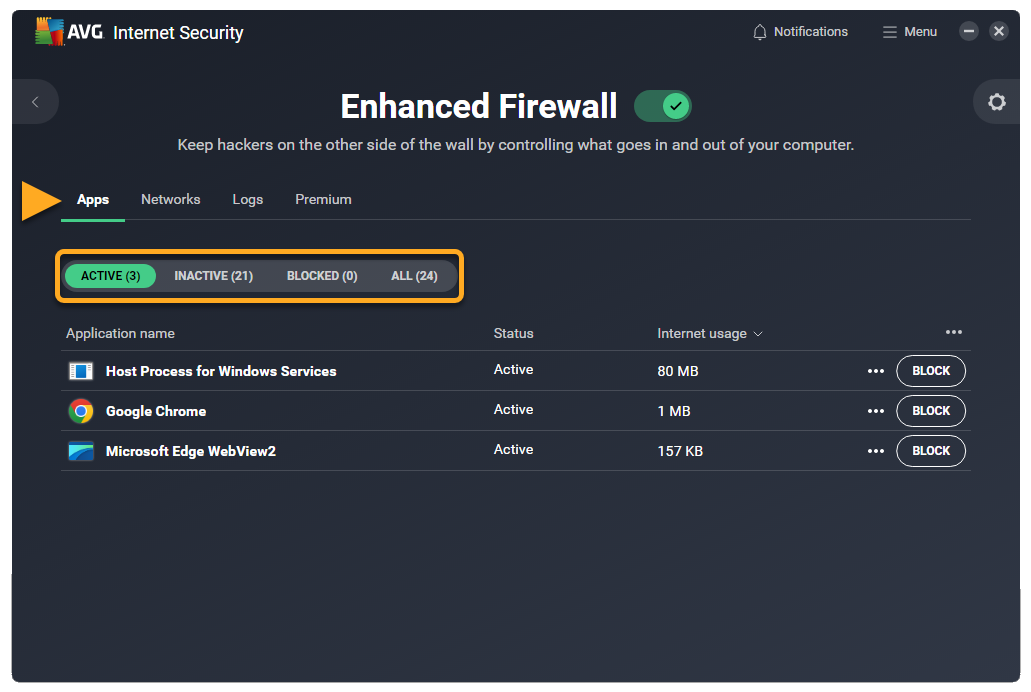
- Ensure the Apps tab is selected, then select one of the following sub-tabs:
- Active: View the apps that are currently using your internet connection.
- Inactive: View the apps that are not currently using your internet connection.
- Blocked: View the apps that are currently blocked from using your internet connection.
- All: View the apps that are installed on your PC.

- The following options are available for each app:
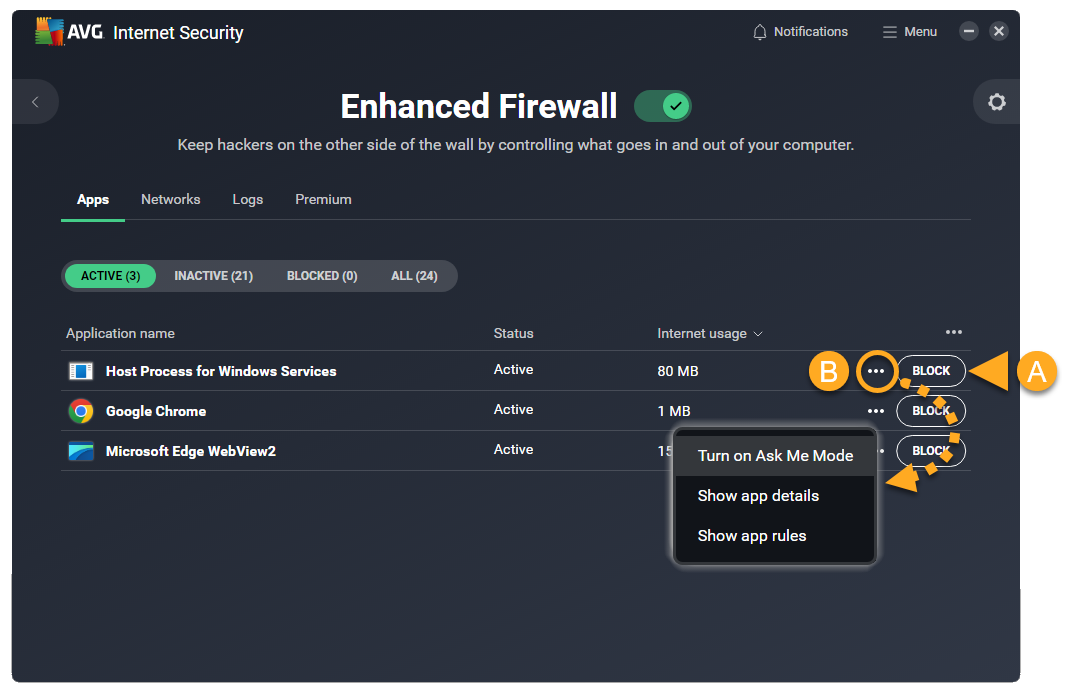
- Click Block in the relevant panel to ensure that Enhanced Firewall always stops this app from connecting to the internet or to other networks.
- Click
⋮More options (the three dots) to choose from the following:- Turn on Ask me Mode: Ensure that Enhanced Firewall prompts you to manually allow or deny each connection attempt for this app.
- Show app details: View basic information about this app.
- Show app rules: Open the advanced Application rules for this app.

Unblock apps
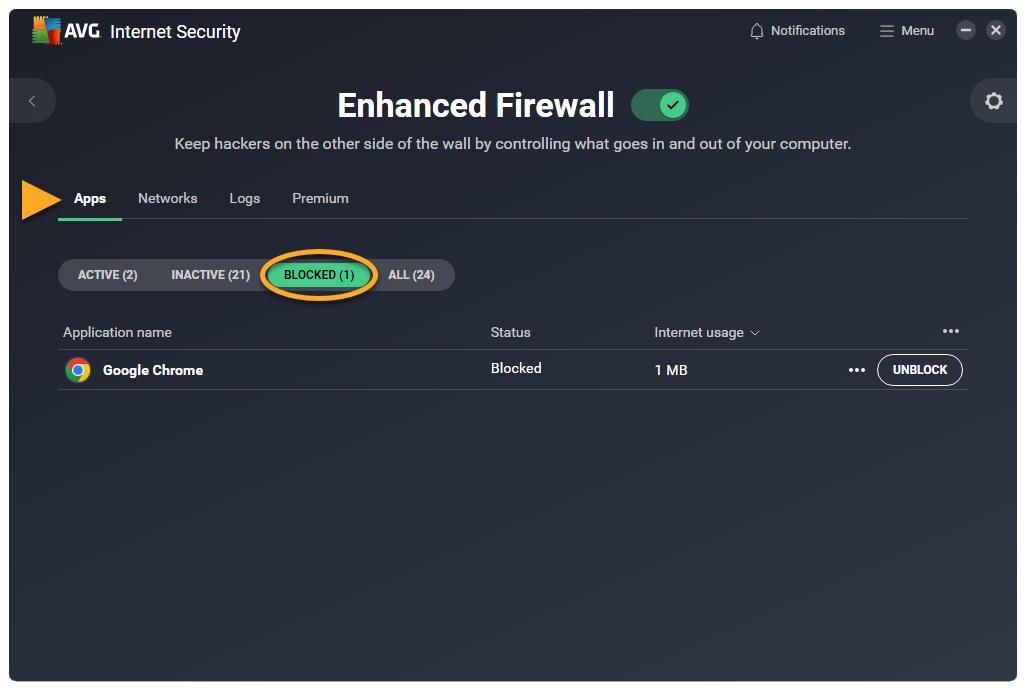
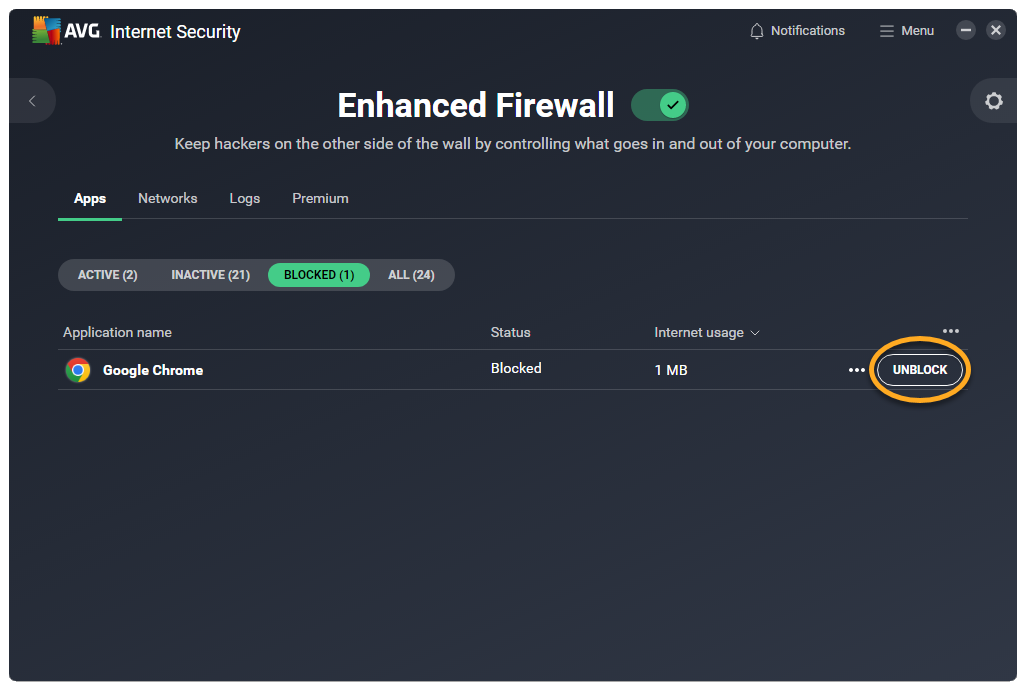
When you block an app, it appears on your list of blocked apps. To unblock an app:
- Ensure the Apps tab is selected, then click the Blocked sub-tab.

- Click Unblock next to the relevant app.

This app can now connect to the internet and to other networks.
Add trusted and untrusted networks
Every time you connect to a new network, Enhanced Firewall detects if the network is private or public, and automatically applies the relevant settings below:
- Private networks (such as your home or work network) require a lower level of security, and are automatically marked as trusted. Each time you connect to a trusted network, Enhanced Firewall permits all communication within the network and applies a lower level of security to enable better connectivity.
- Public networks (such as in a cafe or airport) present a greater security risk, and are automatically marked as untrusted. Each time you connect to an untrusted network, Enhanced Firewall blocks all incoming communication and applies a higher level of security to ensure your privacy and safety.
If necessary, you can manually specify that an individual network is either trusted or untrusted by following the steps below:
- Open AVG Antivirus and select the Web & Email tile.

- Click Open above Enhanced Firewall.

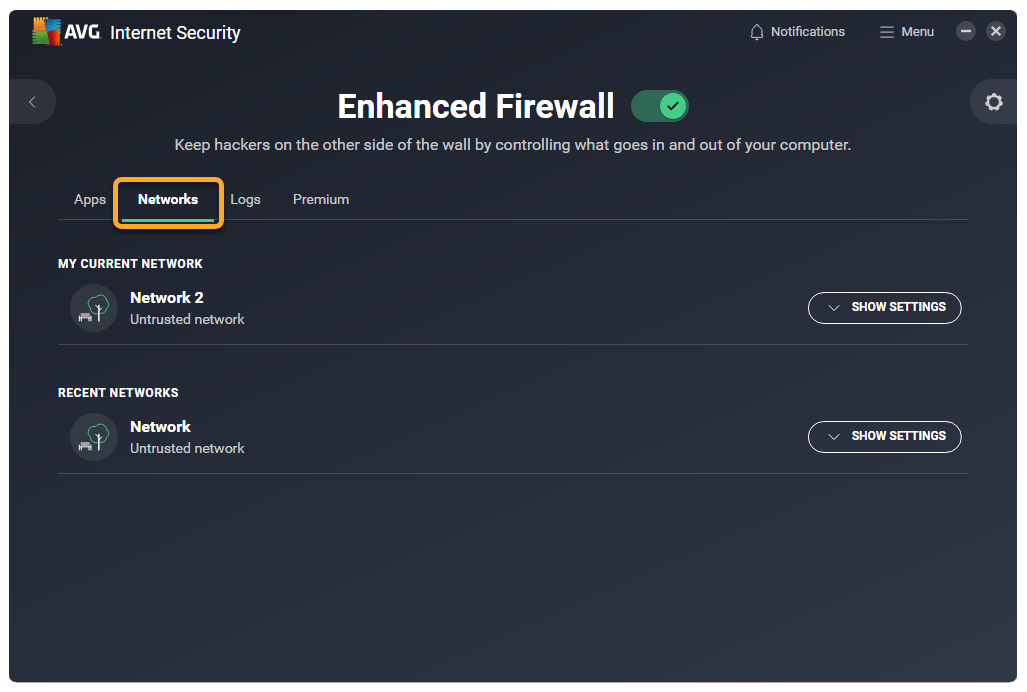
- Select the Networks tab.

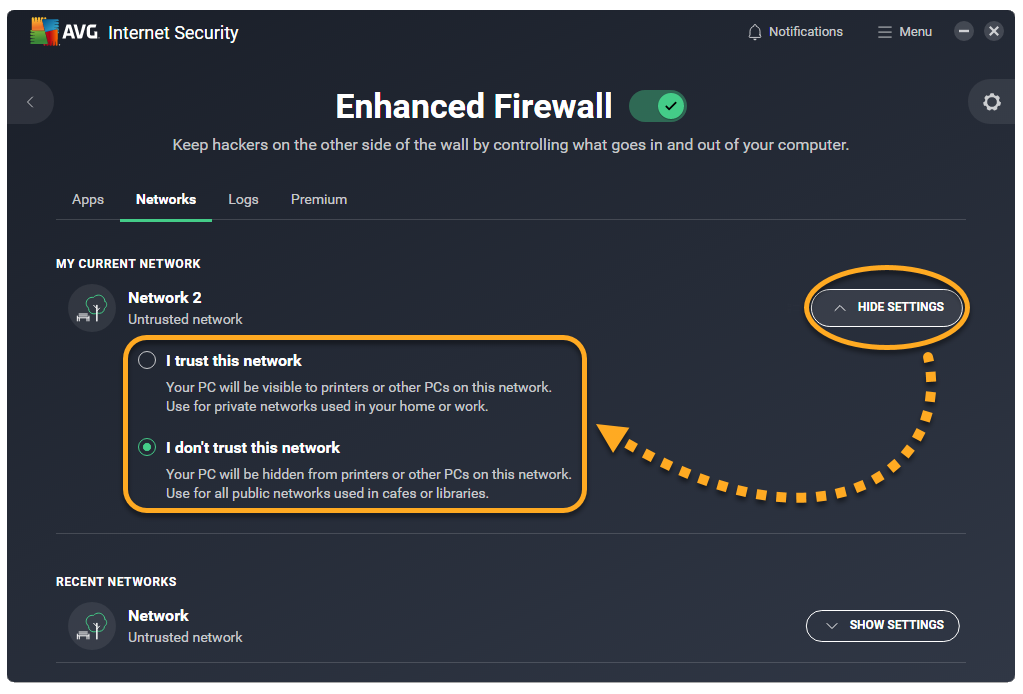
- Click Show settings next to the relevant network, then choose one of the following options:
- I trust this network: The recommended option for a private network. When you select this option, the network is marked as a Trusted network.
- I don't trust this network: The recommended option for a public network. When you select this option, the network is marked as an Untrusted network.

Each time you connect to this network, Enhanced Firewall applies the appropriate settings according to your preferences.
View Enhanced Firewall logs
To view your recent Enhanced Firewall activity:
- Open AVG Antivirus and select the Web & Email tile.

- Click Open above Enhanced Firewall.

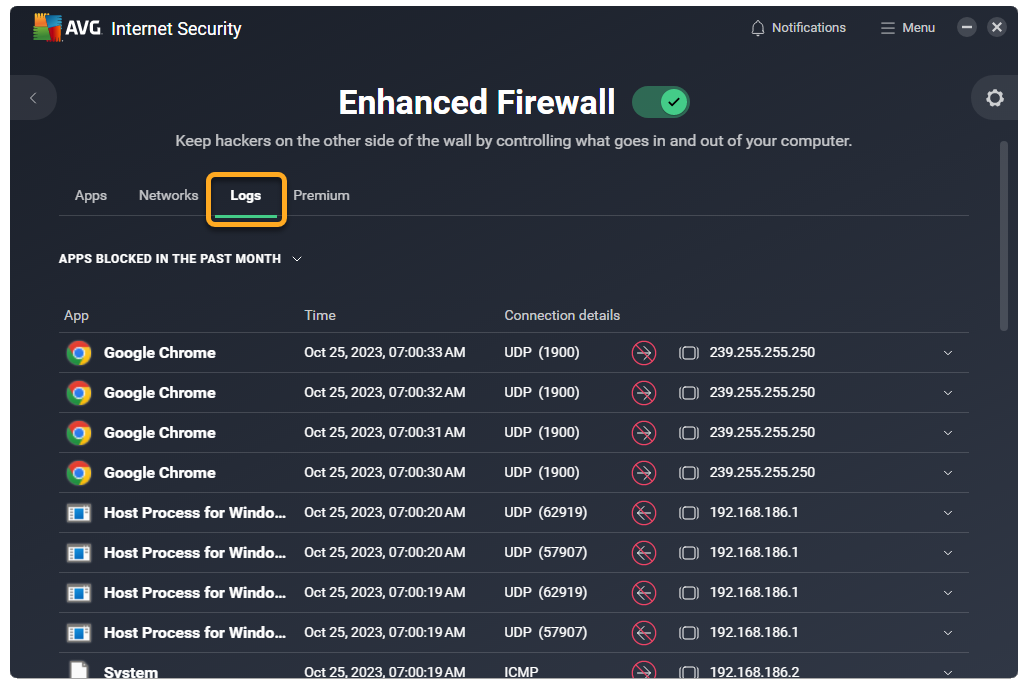
- Select the Logs tab.

- Click the arrow beside Apps blocked in the past month, then select one of following options:
- Blocked apps
- Blocked devices
- Applied rules

The list automatically updates to show your chosen data.
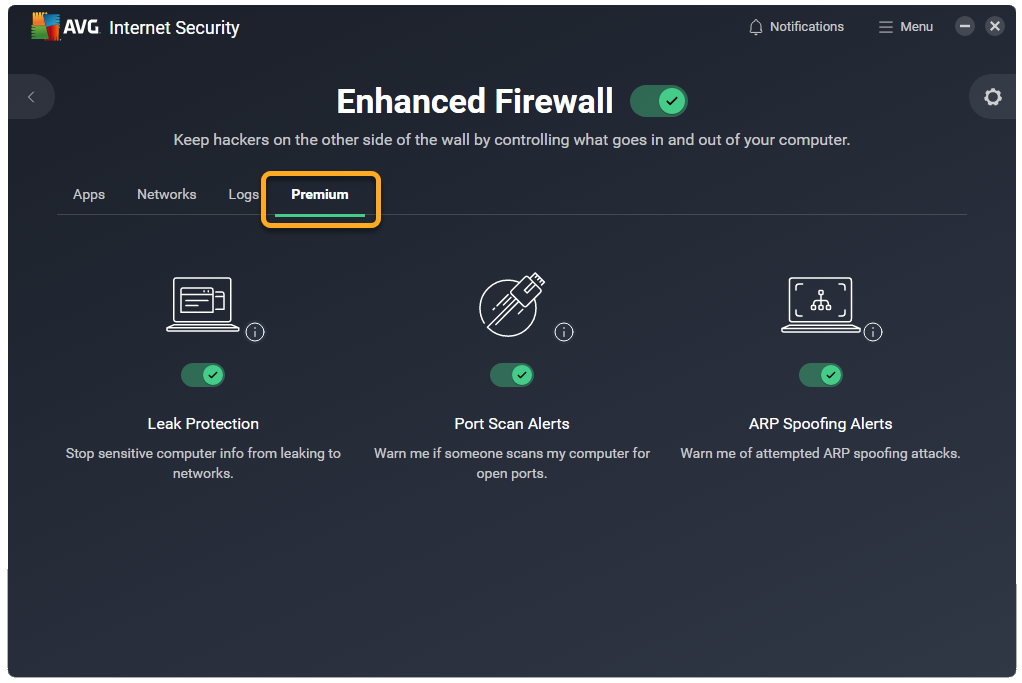
Access premium features
The following premium Enhanced Firewall features are available in AVG Internet Security:
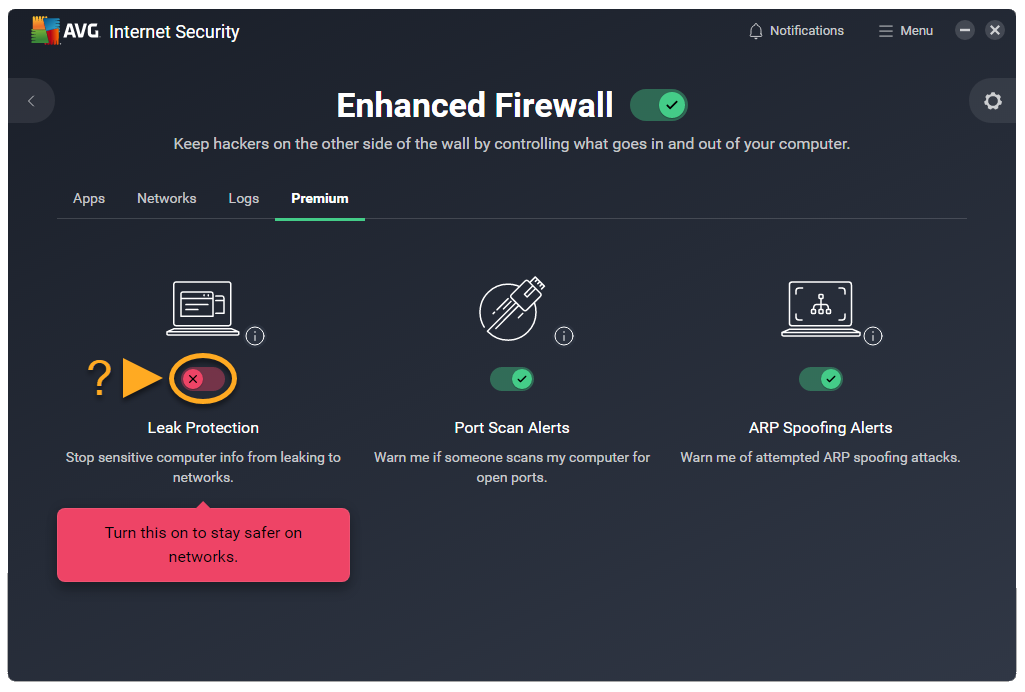
- Leak Protection: Increases your security on public networks by preventing your PC from leaking potentially sensitive information to the network, including your login credentials, computer name, and email address.
- Port Scan Alerts: Alerts you if hackers or malware attempt to scan your PC for open ports.
- ARP Spoofing Alerts: Alerts you if an attacker attempts to intercept your network traffic via an ARP spoofing attack. ARP spoofing is when an attacker exploits the Address Resolution Protocol (ARP) to trick the devices on a network into communicating with an external device that is controlled by the attacker.
To manage the premium Enhanced Firewall features:
- Open AVG Internet Security and select the Web & Email tile.

- Click Open above Enhanced Firewall.

- Select the Premium tab.

- Select your preferred option below:
- Enable a premium feature: Click the red (OFF) slider so that it changes to green (ON).
- Disable a premium feature: Click the green (ON) slider so that it changes to red (OFF).

When these features are enabled, they activate automatically whenever you connect to an untrusted network. This ensures your protection, while avoiding frequent and potentially intrusive false-positive alerts.
For more information about the premium Enhanced Firewall features, refer to the following article:
Advanced settings
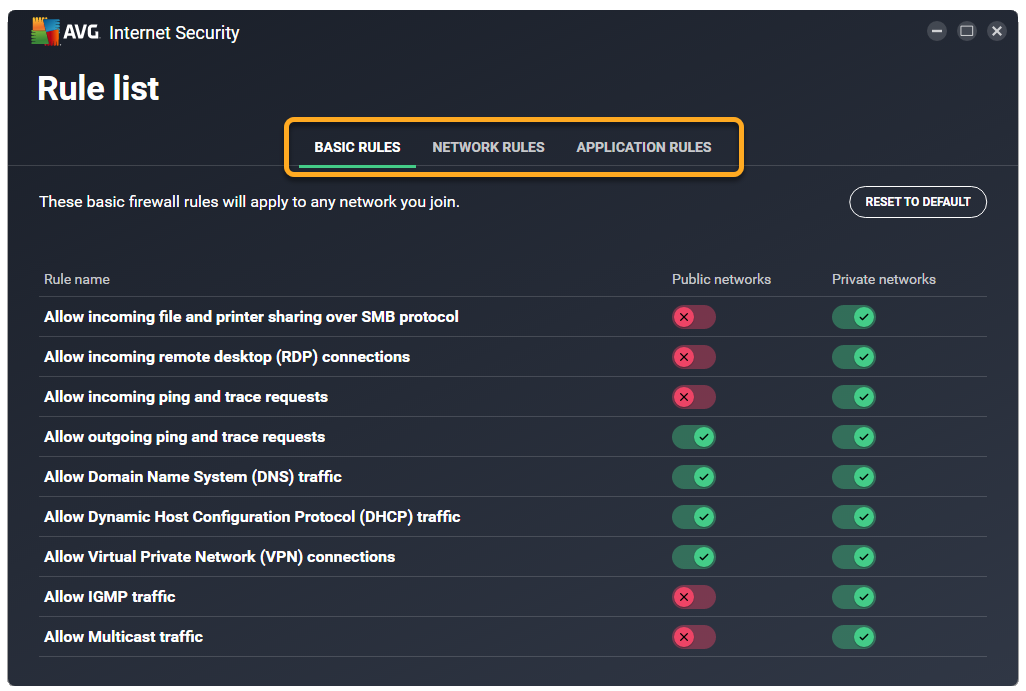
The Enhanced Firewall Rule list contains a list of advanced rules that you can customize to more precisely control Enhanced Firewall behavior.
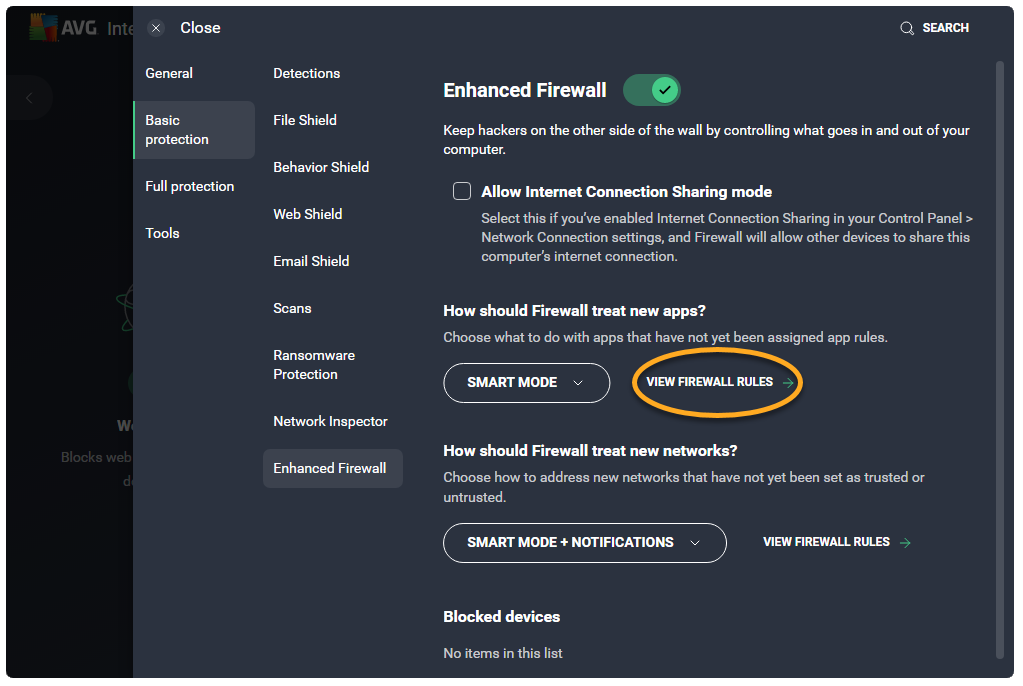
To access advanced Enhanced Firewall rules:
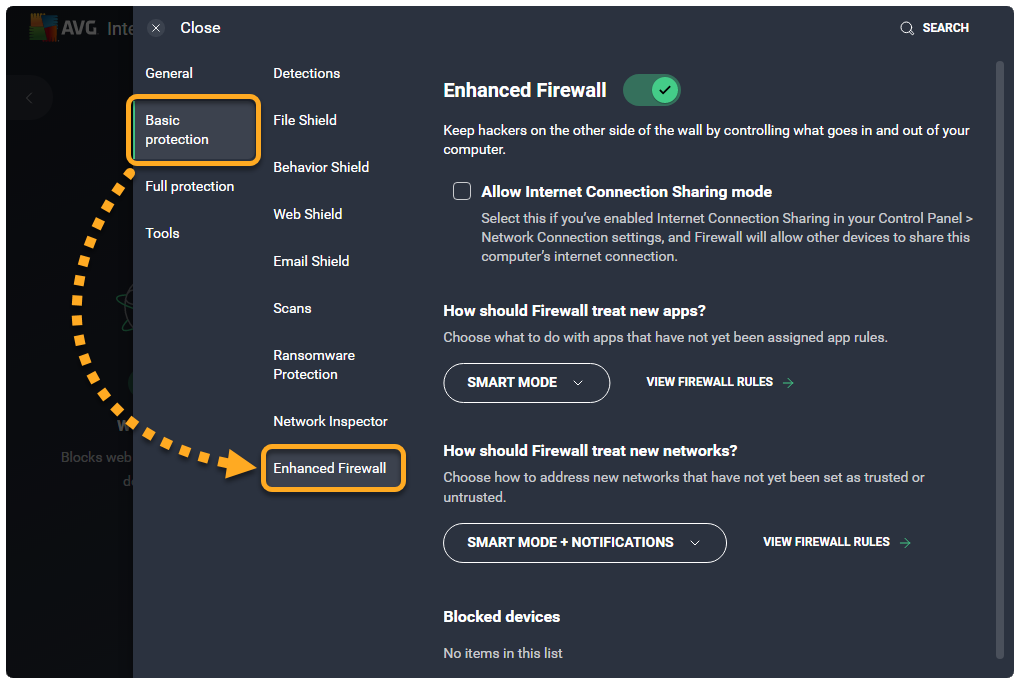
- Open AVG Antivirus and select the Web & Email tile.

- Click
 Settings (the gear icon) in the top-right corner of the screen.
Settings (the gear icon) in the top-right corner of the screen. 
- Click Basic protection ▸ Enhanced Firewall in the left panel.

- Click View Firewall rules.

- Select the relevant tab below:
- Basic rules (previously known as System rules): Are a range of Enhanced Firewall rules that control network traffic for the most common connection types.
- Network rules (previously known as Packet rules): Control whether network traffic is allowed or blocked according to the information contained in network packets.
- Application rules: Determine how Enhanced Firewall behaves towards each application or process when it connects to the internet or to another network.

For detailed information about the options available on each screen, refer to the relevant article below:
Enable or disable Firewall
To ensure your full security, Enhanced Firewall is enabled by default. We recommend keeping Enhanced Firewall enabled at all times, unless you need to disable it temporarily for troubleshooting purposes.
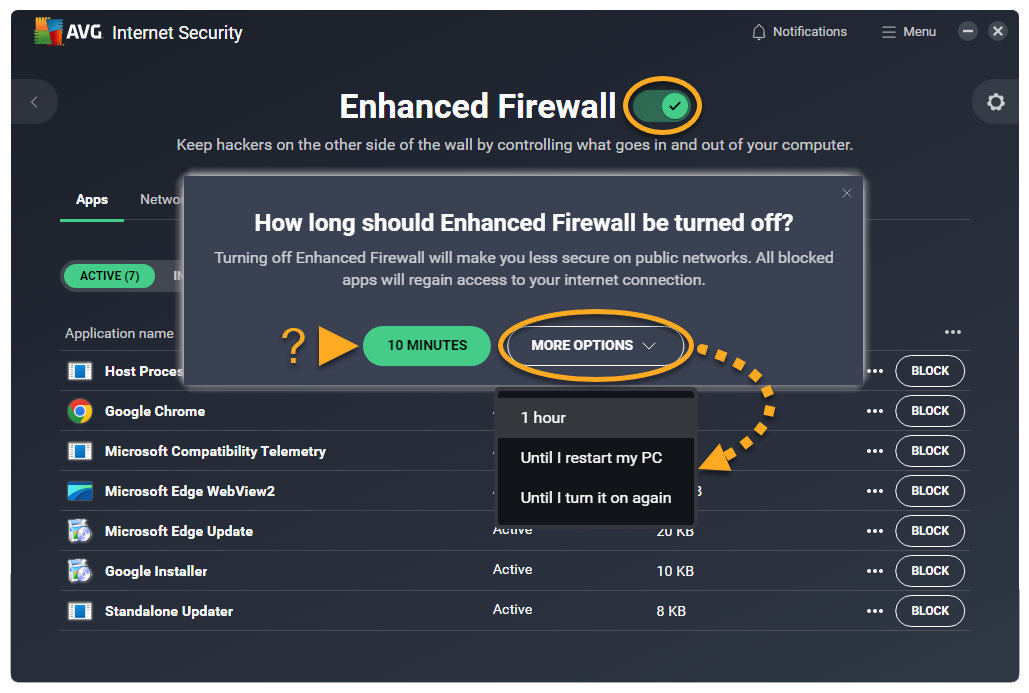
To disable Enhanced Firewall temporarily:
- Open AVG Antivirus and select the Web & Email tile.

- Click Open above Enhanced Firewall.

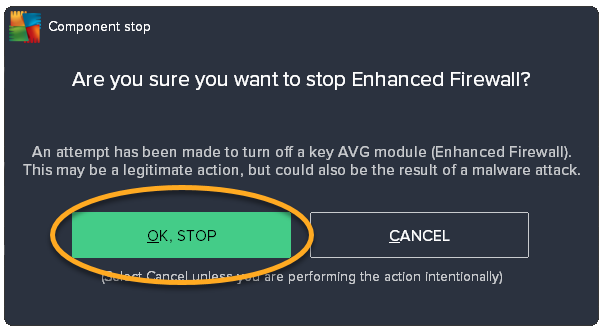
- Click the green (ON) slider, then select a time duration.

- Click OK, stop in the dialog that appears.

Enhanced Firewall is temporarily disabled. To enable Enhanced Firewall, follow steps 1-2 above, then click the slider so that it changes from red (OFF) to green (ON).
Further recommendations
To learn more about the Enhanced Firewall feature in AVG Antivirus, refer to the following article:
- AVG Internet Security 23.x for Windows
- AVG AntiVirus FREE 23.x for Windows
- Microsoft Windows 11 Home / Pro / Enterprise / Education
- Microsoft Windows 10 Home / Pro / Enterprise / Education - 32 / 64-bit
- Microsoft Windows 8.1 / Pro / Enterprise - 32 / 64-bit
- Microsoft Windows 8 / Pro / Enterprise - 32 / 64-bit
- Microsoft Windows 7 Home Basic / Home Premium / Professional / Enterprise / Ultimate - Service Pack 1 with Convenient Rollup Update, 32 / 64-bit